Overview
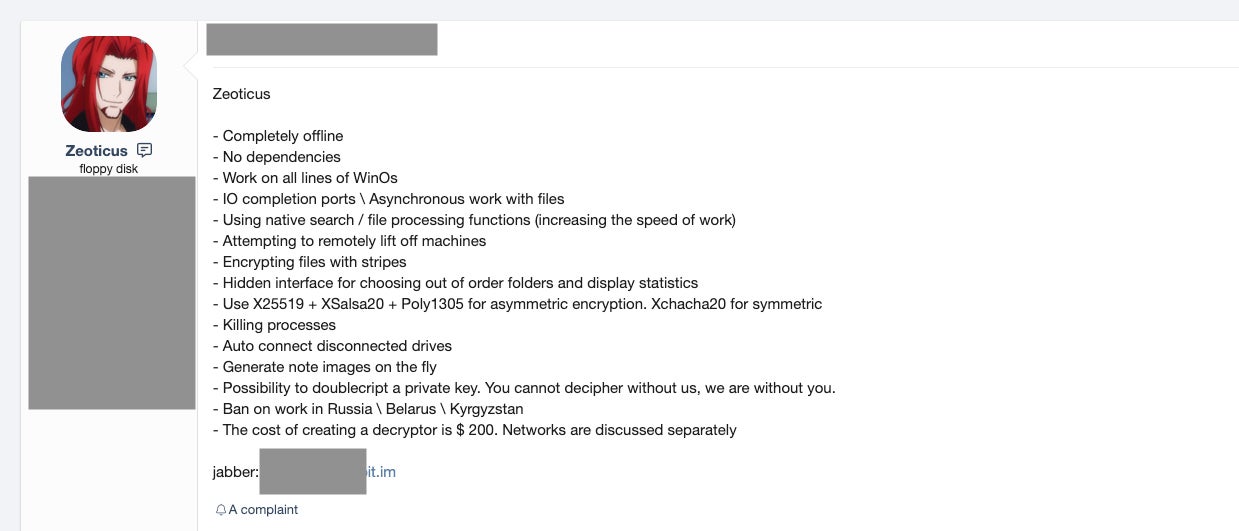
Zeoticus ransomware first appeared for sale in various underground forums and markets in early 2020. Initially, the ransomware was offered as a complete custom build for an undisclosed fee. The ransomware is currently Windows-specific and, according to the developers, functions on all “supported versions of Windows”.
Unusually, there are no connectivity requirements for the payloads to execute. Zeoticus ransomware will execute fully offline, with no dependence on a C2 (Command & Control). It is also worth noting that the malware is designed not to function in some regions, specifically Russia, Belarus, and Kyrgyzstan. Like many other families, use within the CIS is discouraged in order to avoid any backlash from regional government and law enforcement agencies.
Zeoticus Development
Since late 2020 and moving into early 2021, the vendor has continued to maintain and offer updates on the Zeoticus service.
In December 2020, samples of Zeoticus 2.0 were observed and reported in the wild. Multiple researchers and security vendors began to take notice and analyze these updated samples ( e.g., tweet from @demonslay335)
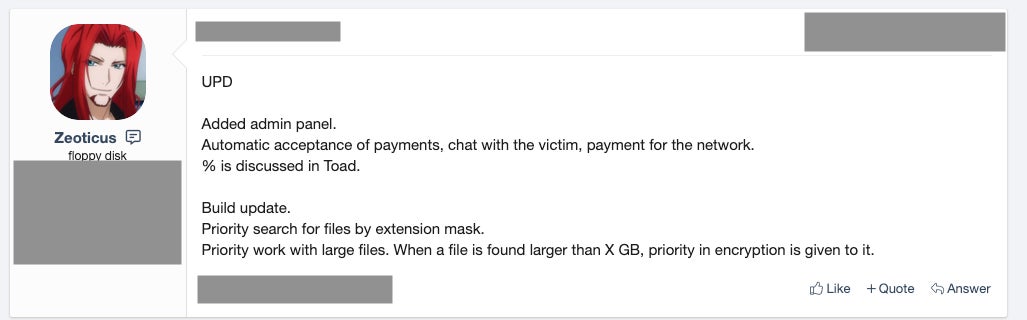
A recent public announcement includes updates on file extension-based identification and performance around the prioritization and encryption of extremely large files.
Most of the updates in Zeoticus 2.0 are focused on speed and efficiency. Specific encryption algorithms (both symmetric and asymmetric) have been employed based on their speed (e.g., Poly1305 is used for signing the primary encryption key rather than something like SHA1).
Other notable features include compatibility with “all lines of Windows OSs”, with some indications that the ransomware will even run on Windows XP and earlier.
The ransomware also has the ability to discover and infect remote drives and to discover and terminate processes that could interfere with the encryption process.
Execution and Persistence
Upon execution, pertinent files are identified based on extension. The encryptable-extension list is fully customizable and in the control of the attacker.
When launched, the malware makes a few copies of itself in the following locations:
C:Windows %AppData%
Following this, Zeoticus proceeds to kill off a number of running processes (via taskkill.exe) as follows:
sqlagent.exe sqlbrowser.exe sqlservr.exe sqlwriter.exe oracle.exe ocssd.exe dbsnmp.exe synctime.exe mydesktopqos.exe agntsvc.exe isqlplussvc.exe xfssvccon.exe mydesktopservice.exe ocautoupds.exe agntsvc.exe agntsvc.exe agntsvc.exe encsvc.exe firefoxconfig.exe tbirdconfig.exe ocomm.exe mysqld.exe mysqld-nt.exe mysqld-opt.exe dbeng50.exe sqbcoreservice.exe excel.exe infopath.exe msaccess.exe mspub.exe onenote.exe outlook.exe powerpnt.exe sqlservr.exe thebat64.exe thunderbird.exe winword.exe Wordpad.exe
Zeoticus utilizes the ping command to facilitate the deletion of its own binaries, redirecting the output of the command to >nul & del to achieve this.
/c ping localhost -n 3 > nul & del %s
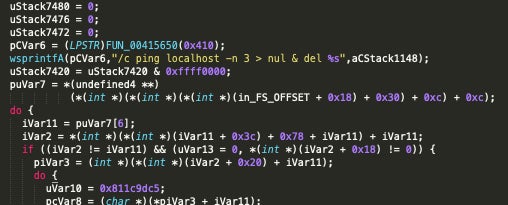
The following WMI query is then issued to gather additional information about the local environment:
start iwbemservices::execquery - rootcimv2 : select __path, processid, csname, caption, sessionid, threadcount, workingsetsize, kernelmodetime, usermodetime, parentprocessid from win32_process where ( caption = "msftesql.exe" or caption = "sqlagent.exe" or caption = "sqlbrowser.exe" or caption = "sqlservr.exe" or caption = "sqlwriter.exe" or caption = "oracle.exe" or caption = "ocssd.exe" or caption = "dbsnmp.exe" or caption = "synctime.exe" or caption = "mydesktopqos.exe" or caption = "agntsvc.exe" or caption = "isqlplussvc.exe" or caption = "xfssvccon.exe" or caption = "mydesktopservice.exe" or caption = "ocautoupds.exe" or caption = "agntsvc.exe" or caption = "agntsvc.exe" or caption = "agntsvc.exe" or caption = "encsvc.exe" or caption = "firefoxconfig.exe" or caption = "tbirdconfig.exe" or caption = "ocomm.exe" or caption = "mysqld.exe" or caption = "mysqld-nt.exe" or caption = "mysqld-opt.exe" or caption = "dbeng50.exe" or caption = "sqbcoreservice.exe" or caption = "excel.exe" or caption = "infopath.exe" or caption = "msaccess.exe" or caption = "mspub.exe" or caption = "onenote.exe" or caption = "outlook.exe" or caption = "powerpnt.exe" or caption = "sqlservr.exe" or caption = "thebat64.exe" or caption = "thunderbird.exe" or caption = "winword.exe" or caption = "wordpad.exe")
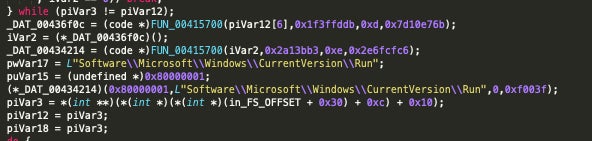
All samples analyzed across Zeoticus 1.0 and 2.0 create the Registry Run key to achieve persistence:
REGISTRYUSER----SoftwareMicrosoftWindowsCurrentVersionRun
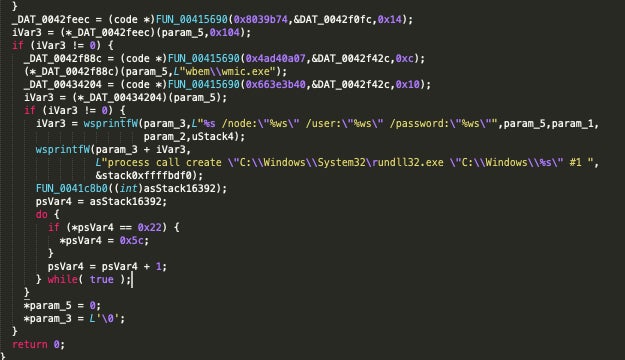
The registry entry (Run) is set to launch an instance of the Zeoticus payload from C:Windows:
Encryption and Ransom Note
The ransomware uses a combination of asymmetric and symmetric encryption. XChaCha20 is utilized on the symmetric side, while the combination of Poly1305, XSalsa20 and Curve25519 is used for the asymmetric side.
Encrypted files are modified with extensions that include the contact email address of the attacker(s) along with the string “2020END”, which is no doubt a reference to the new year.
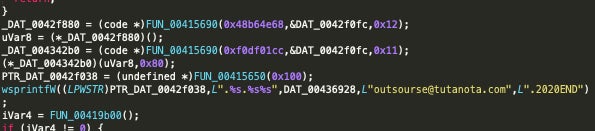
In parallel with the encryption of the host’s data, Zeoticus mounts a new volume which contains the ransom note. Victims are instructed to contact the attacker via email as opposed to using an onion-based payment portal or similar. Additionally, the ransomware will drop a copy of the ransom note to the root of the system drive ( e.g., C:WINDOWSREADME.html).
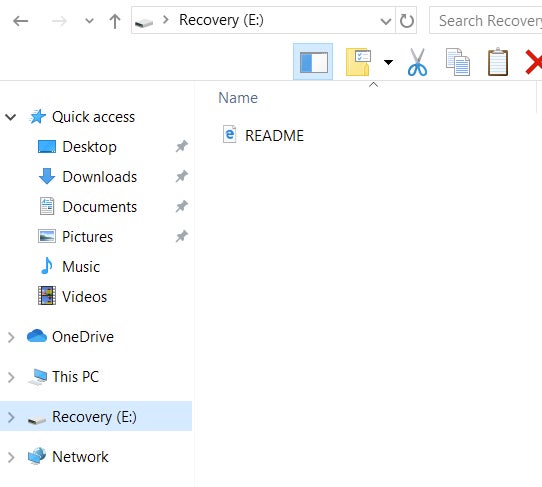
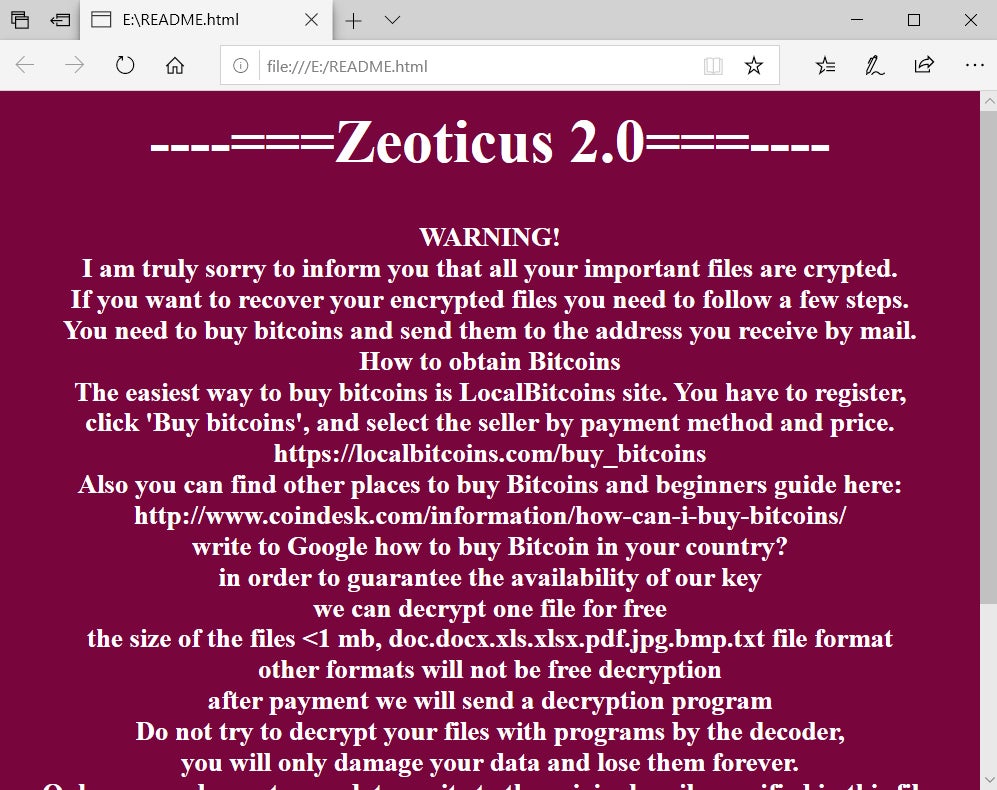
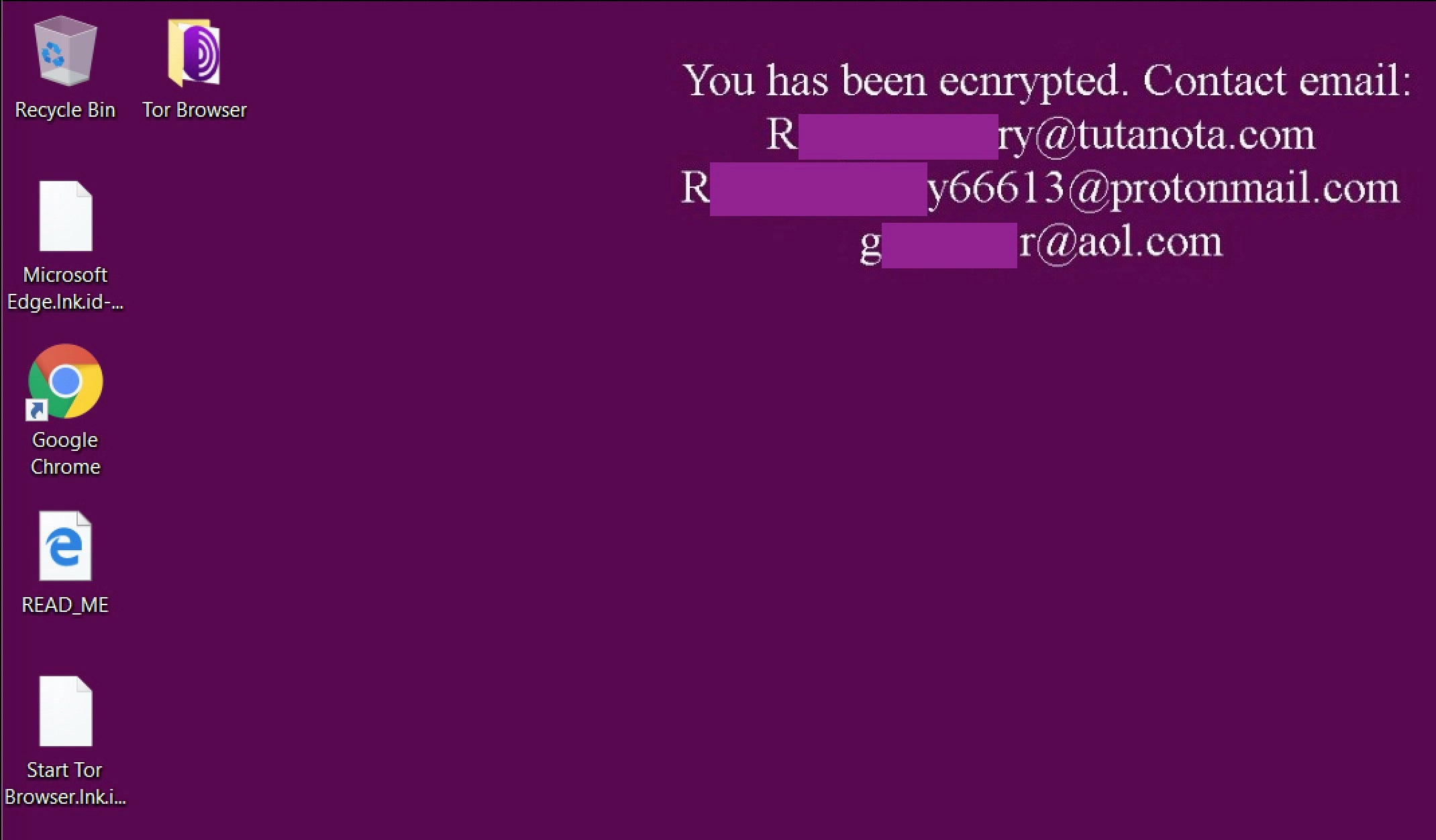
This is one of the more noticeable differences between Zeoticus 2.0 and 1.0. That is, in v1.0, the desktop wallpaper was actually altered with the victim instructions as opposed to mounting the new volume.
Conclusion
Attackers are continuing to improve upon their techniques and tactics. Active ransomware infections are getting increasingly difficult to control, contain, and mitigate. Prevention of these attacks is more important than ever given the difficulty of recovering from a catastrophic ransomware attack. We encourage all to review their security posture and take any necessary steps to improve their protections and reduce their overall exposure. Visibility and education go a long way here. A thorough and accurate understanding of the environment is key in prioritizing controls and reducing risk. It is also important to educate end users on the methods used by these attackers, and encourage them to report any suspicious activity they observe. Finally, ensure that all technological controls are installed and implemented properly, and are up to date with the latest patches.
IOCs
SHA256
33703e94572bca90070f00105c7008ed85d26610a7083de8f5760525bdc110a6
279d73e673463e42a1f37199a30b3deff6b201b8a7edf94f9d6fb5ce2f9f7f34
SHA1
25082dee3a4bc00caf29e806d55ded5e080c05fa
d3449118b7ca870e6b9706f7e2e4e3b2d2764f7b
MITRE ATT&CK
Data from Local System – T1005
Credentials from Password Stores – T1555
Modify Registry – T1112
Query Registry – T1012
Remote System Discovery – T1018
System Information Discovery – T1082
Peripheral Device Discovery – T1120
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder – T1547.001
Data Encrypted for Impact – T1486




