Thanos ransomware burst onto the scene in late 2019, advertised in various forums and closed channels. Thanos is a RaaS (Ransomware as a Service) which provides buyers and affiliates with a customized tool to build unique payloads.
This tool is far more complex and robust than many previous builder-based ransomware services such as NemeS1S and Project Root. The generated payloads can be configured with numerous features and options. Many of the options available in the Thanos builder are designed to evade endpoint security products, and this includes the use of the RIPlace technique. To date, Thanos appears to be the only widely-recognized threat making use of RIPlace, although the feature was not always part of the Thanos toolset.
Initial Feature Set
The original advertised general feature set in November 2019 included:
- Written in .NET
- Support for Windows 7 upward
- Simple and attractive builder interface
- Automatic updates to the builder tool(s)
- Strong encryption, via “American Government Encryption standard for communications with a large encryption key.”
- Unique encryption keys per host
- Configurable ransom note, and extensions
- Small client footprint
In those same early posts, the following more “advanced” features were highlighted:
- Multiple persistence options
- Client (payload) can be set as a critical payload (resulting in BSOD upon attempts to terminate)
- Randomized assembly data
- Anti-VM / VM-evasion
- Termination of Windows Defender and other AV products
- 100GB Maximum filesize for encryption, which can be expanded
- FTP-based logging
- Mutex-based duplication avoidance
- Configurable spreading options (network and removable drive attacks)
- Strong “obfuscation against forensics”
- Dynamic code generation
- Polymorphic clients
- Various compilation platform options
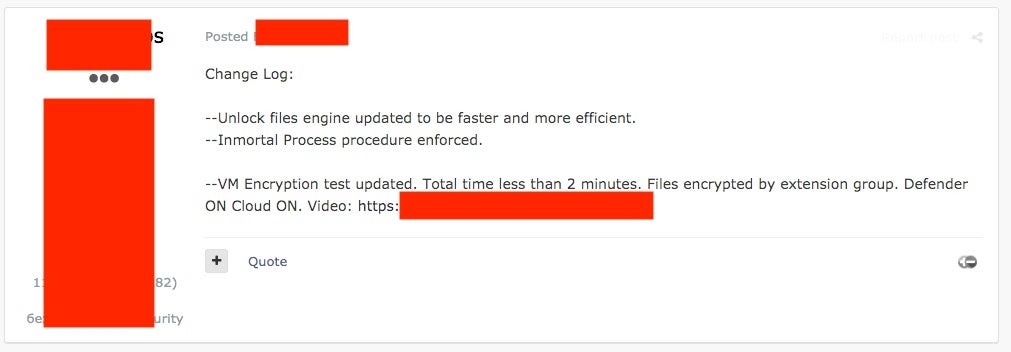
Development with RIPlace
The option to include the RIPlace technique appeared in early January 2020 and was subsequently made available to existing “customers” and “affiliates”.
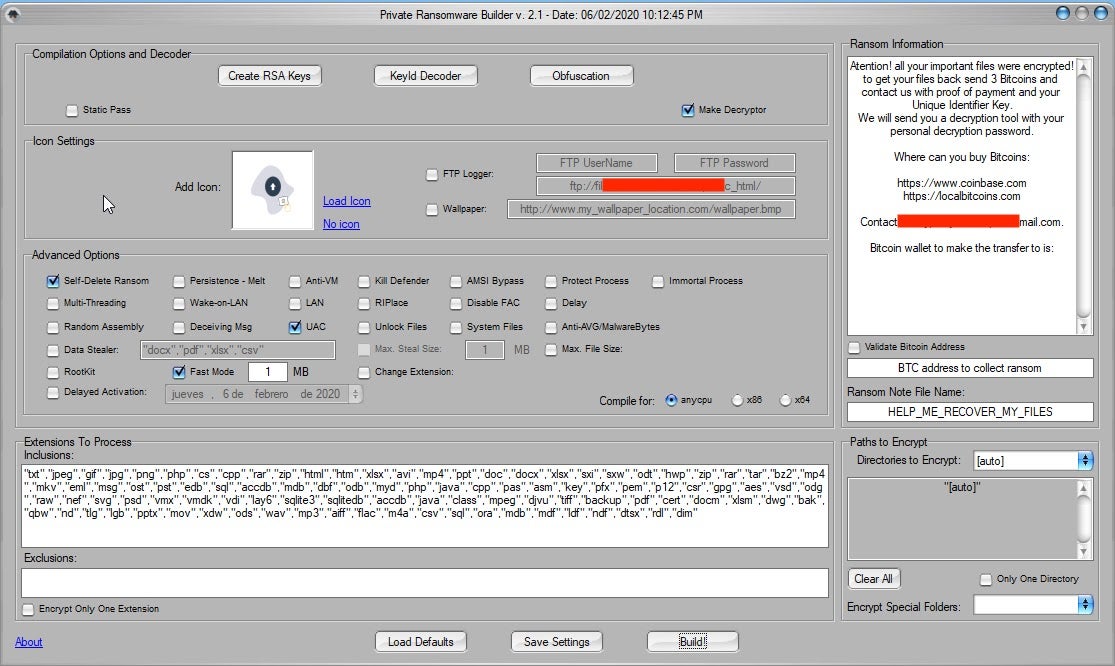
Between February and June 2020, the following features were added to the toolset:
- RIPlace
- Updated FTP-based reporting
- Built-in Rootkit feature (ransomware is not stealth and invisible to Task Manager during encryption)
- Tool interface improvements
- Immortal process support expansion
- Encryption speed enhancements (advertised to fully encrypt hosts in less than 2 minutes)
- Rootkit option expanded to support Windows 7, 8, 10 on both x86 and x64 architectures
- LAN-wide ransom notes can now appear at Windows Login
- Runtime dyncheck for the ransomware client
- Support for distinguishing between upper and lower-case file extensions
- Updated Client expiration options
- LAN share encryption without having to map drives
- Updated runtime compilation
- Routine cloud-based “Refud” (updates to AV evasion)
In April 2020, an option to simply encrypt “All Files” independent of the file extensions was added along with improved network encryption methods.
Rapid Iteration Continues
More notable changes were made to the toolset in May 2020. These updates include:
- Disabling of 3rd party backup solutions (in addition to AV product termination)
- Ransomware client now both self-deletes AND overwrites its’ relevant sectors to increase complexity of forensics
- File-permission changing to capture (exfil) or encrypt more files
- Users can now be fully locked out of their Windows/Microsoft accounts
- Bootlocker feature will display the ransom note at boot level (non UEFI / Secure Boot-protected clients)
- Removal of Windows Defender signature files
- Safe-mode encryption option
- Network-adjacent hosts can also be encrypted in safe-mode
Recent updates of the toolset extend into June 2020:
- Faster and more reliable directory traversal algorithm in the decryption process
- LAN infection procedure is now Wake-on-LAN aware and capable
- On-the-fly of newly connected drives. If hosts are actively infected, any connected drive (ex: USB) will be encrypted
- Encryption routine can impersonate SYSTEM via process hollowing
- LAN infection using varied/rotating accounts or identities
- Network encryption via tokens that differ from the current user
- Expanded support of encryption on Windows Server 2012
The actors behind Thanos are very aware of their “clients” needs and the attention they are getting from the security industry. The most recent update included some level of code rebuilding in order to continue to evade security products that have updated their signatures based on all the recent media attention. That should be a subtle hint to move aware from signature based products if you are still on the fence with that one. This is not unique to Thanos. Malware authors are constantly adjusting payload to avoid signature-based detection.
Encryption Methodology
Thanos’ encryption methodology has varied across the evolution of its payloads. Based on both our own analysis and that of others (Recorded Future), Thanos will employ a random 32-byte long string at runtime as the passphrase for file encryption (AES). The string is subsequently encrypted with the attacker’s public key and added into the generated ransom note(s). As a result, recovery of encrypted data is not possible without the corresponding private key.
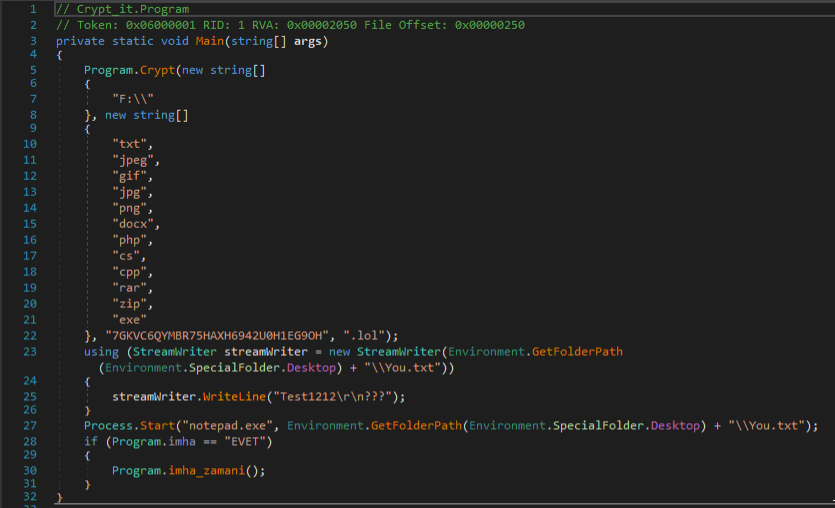
Delivery and Behavior
The primary delivery method of Thanos ransomware (observed in-the-wild) is phishing emails. Recent campaigns have used standard financial-based lures in the email message (tax refund details, various invoice schemes, economic stimulus package updates).
Upon launch, the ransomware will, based on the build and configuration, attempt to terminate processes related to a plethora of security products and system utilities. This is done to ensure both proper and thorough encryption, but also to increase the capability of harvesting data and files.
The following commands were pulled from sample:
23d7693284e90b752d40f8c0c9ab22da45f7fe3219401f1209c89ac98a4d7ed3:
stop avpsus /y stop McAfeeDLPAgentService /y stop mfewc /y stop BMR Boot Service /y stop NetBackup BMR MTFTP Service /y config SQLTELEMETRY start= disabled config SQLTELEMETRY$ECWDB2 start= disabled config SQLWriter start= disabled config SstpSvc start= disabled
Standard tricks to disable and delete Volume Shadow Copies are also taken. These commands can be seen in the same sample:
Delete Shadows /all /quiet resize shadowstorage /for=c: /on=c: /maxsize=401MB resize shadowstorage /for=c: /on=c: /maxsize=unbounded resize shadowstorage /for=d: /on=d: /maxsize=401MB resize shadowstorage /for=d: /on=d: /maxsize=unbounded resize shadowstorage /for=e: /on=e: /maxsize=401MB resize shadowstorage /for=e: /on=e: /maxsize=unbounded resize shadowstorage /for=f: /on=f: /maxsize=401MB resize shadowstorage /for=f: /on=f: /maxsize=unbounded resize shadowstorage /for=g: /on=g: /maxsize=401MB resize shadowstorage /for=g: /on=g: /maxsize=unbounded resize shadowstorage /for=h: /on=h: /maxsize=401MB resize shadowstorage /for=h: /on=h: /maxsize=unbounded
The following suspicious WMI queries are present as well:
start iwbemservices::execquery - select __path, processid, csname, caption, sessionid, threadcount, workingsetsize, kernelmodetime, usermodetime, parentprocessid from win32_process where ( caption = "mspub.exe")
start iwbemservices::execquery - select __path, processid, csname, caption, sessionid, threadcount, workingsetsize, kernelmodetime, usermodetime, parentprocessid from win32_process where ( caption = "mydesktopqos.exe")
start iwbemservices::execquery - select __path, processid, csname, caption, sessionid, threadcount, workingsetsize, kernelmodetime, usermodetime, parentprocessid from win32_process where ( caption = "mydesktopservice.exe")
start iwbemservices::execquery - select caption from win32_operatingsystem
Summary
Thanos is another example of just how robust modern ransomware services can be, and how far they have come since the early days of RaaS offerings such as Ransom32 and EncryptorRaaS. With a focus on evasion and active development of features in response to customer needs, Thanos is cementing its position as a primary tool for low-to-mid level criminals looking for an effective, easy-to-use malware tool that will both yield results and allow them to customize for their own specific target groups.
IOCs
SHA1
f086a802887c4b3ed9be69ffc018fb6ffb324f5e
15a00d3aba362aade900374b6d159de98e8eac62
0ecff2f818565e7eb28d3a7b7d295459a868e920
ffcc533b3b5630f405ff9e6274fc273f1bd33594
f5664b367a841643728cd90d0cb61df9e58fa4d7
4c6e634075781724cba954a76d1d831d077b7257
da0cd782f32088c0df8cd62deda1c61b4cedd6fb
caef3905436bdf99bda6a3de64b162630c527375
6be2e40bd6901462f9d87fbee63740a3971d1a75
31bd11c9d4dd19185a2ea42507ba8a3651198335
5b1d1de92d8b8163ac70281d6afa3113d0f86362
4e04822d6b8c3087be0550dba96f0c80d84359f8
a86ba83804da1f7d2675d5994c724995fef09771
c5517ca6e843efb0a4d2989e6ba16dde6cf7da65
ae42c46c6b8a5a60c232665abd6c9bc469021512
18529b6bef216231c34b2701eb3894ca2dd3a5ba
5f44342dc0cb0c4ef3a3b3dad1e974e9c6eb9120
f3264a5ecd6e1b3aef2884b1c35028eedcf442dc
b4fe4ce027afeb9ca0b88b52891fb7c73d822d10
018a392975a8731735ef709e6418e5af19db3756
db49455bbc76eb00a99e803aa46d5681ac60b17b
1867a1100203ea14f9496b938c23b44a3b31ec40
SHA256
7e6db426de4677efbf2610740b737da03c68a7c6295aca1a377d1df4d35959e5
34b93f1989b272866f023c34a2243978565fcfd23869cacc58ce592c1c545d8e
7a7a5110cb9a8ee361c9c65f06293667451e5200d21db72954002e5725971950
cea80fe543aec9c6b4a4628ec147e8a41cac766c2cd52c0ca86a19f9ef348fc3
17314793d751b66f4afc1fac1c0ab0c21f2c9f67e473e8ba235bc79d7e0ea1b0
d1b634201a6158a90f718a082c0fe0ee1769ff4b613dd9756a34318fa61eea47
5b5802805784b265c40c8af163b465f1430c732c60dd1fbec80da95378ae45b7
ff1a88c2ad5df435a978c63d21a6ab0642134785284b01137e18dd235197b66d
befc6ff8c63889b72d1f5aec5e5accc1b4098a83cd482a6bb85182ecd640b415
81e81f0bbbdb831eda215033b7a7dbf2eed3812f4e58118f181a8e99e613179e
23d7693284e90b752d40f8c0c9ab22da45f7fe3219401f1209c89ac98a4d7ed3
989a9d2e08fcba4059ebc55afc049f34d2a12bfdd1e14f468ee8b5c27c9e7bda
794369bc9a06041f906910309b2ce45569a03c378ff0468b6335d4f653f190ab
855dcd368dbb01539e7efa4b3fefa9b56d197db87b1ba3ede5e1f95927ea2ca3
8a2b54d273d01f8d5f42311d5402950bb9983648a39b943c729314a97ede15a2
09fd6a13fbe723eec2fbe043115210c1538d77627b93feeb9e600639d20bb332
edcac243808957cc898d4a08a8b0d5eaf875f5f439a3ca0acfaf84522d140e7e
f0c0c989b018ee24cbd7548cec4e345fd34f491d350983fddb5ddc1ad1f4ba9f
10dc9cb12580bc99f039b1c084ca6f136047ac4d5555ad90a7b682a2ffac4dc5
a95f9d82097bdfa2dd47e075b75d09907d5913e5c15d05c926de0d8bbce9698f
f7d7111653c43476039efd370fb39fcdb2c22a3f1bb89013af643b45fb3af467
53806ba5c9b23a43ddbfa669798d46e715b55a5d88d3328c5af15ba7f26fbadd




