[Updated April 20, 2020]
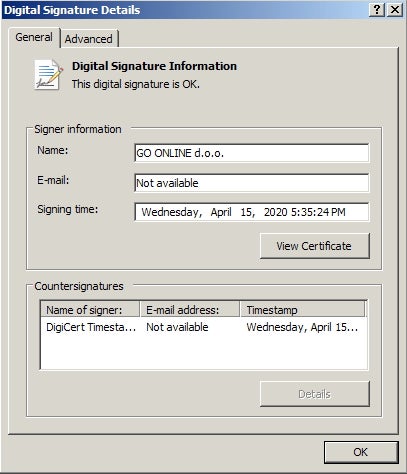
On April 17th, it was reported that a large enterprise-class, managed service provider (Cognizant) fell victim to a Maze ransomware attack. This particular campaign includes a signed DLL payload (kepstl32.dll). Upon infection, the trojan will drop a customized desktop image into %temp%, and then traverse the disk, encrypting supported file-types. A copy of the ransom instructions “DECRYPT-FILES.txt” is dropped into each folder containing encrypted files. As with previous variants of Maze, the trojan will attempt to inhibit recovery by deleting shadow copies via WMIC.exe (wmic.exe shadowcopy delete) Relevant Digital Signature details are as follows:
- Signer Identity: GO ONLINE D.O.O. (Verified, Cert id: GO ONLINE D.O.O.)
- Serial Number: 26 91 74 f9 fe 7c 6e d4 e1 d1 9b 26 c3 f5 b3 5f
- Issuer: CN = Sectigo RSA Code Signing CA
- Subject: CN = GO ONLINE d.o.o.
SentinelOne’s Endpoint Protection Platform is capable of detecting and preventing malicious artifacts associated with the latest waves of Maze ransomware.
[December 19, 2019]
The group behind the Maze ransomware campaigns has been keeping quite busy as of late. We have touched on this threat previously. However, given some recent events and revelations, an update is absolutely warranted.
Background to Maze Ransomware
Maze was initially observed in May of 2019. It was a noted component of steady, yet unremarkable, extortion campaigns. However, in approximately the last two months we have seen a sizable uptick in Maze campaigns, including many notable, high-profile attacks. The actors behind Maze have previously claimed credit for attacks on both Allied Financial as well as the City of Pensacola Florida. More recently, the so-called “Maze Crew” has shifted to a more aggressive and public phase of attack. They are now publicly ‘outing’ targeted companies that chose not to comply with their criminal demands. We will circle back to that point a bit later in this post.
Maze Ransomware: Encrypt, Exfiltrate and Extort
There are a few traits that really set Maze apart from its contemporaries in the malware family universe. Primarily, the goal extends beyond the direct encryption of data local to the targeted environment. While that does occur, there is also functionality to exfiltrate files to remote resources under the attacker’s control.
At this point, they can not only demand money to decrypt the data on compromised endpoints but also extort the victim in return for not leaking the exfiltrated data to the public. Many ransomware victims are able to recover encrypted data without having to succumb to the demands of the malware authors. In these campaigns though, that alone may not save them. Preventing the release of sensitive or confidential data brings about a whole new set of problems, and the ability to “resolve matters quietly” becomes more of a reach.
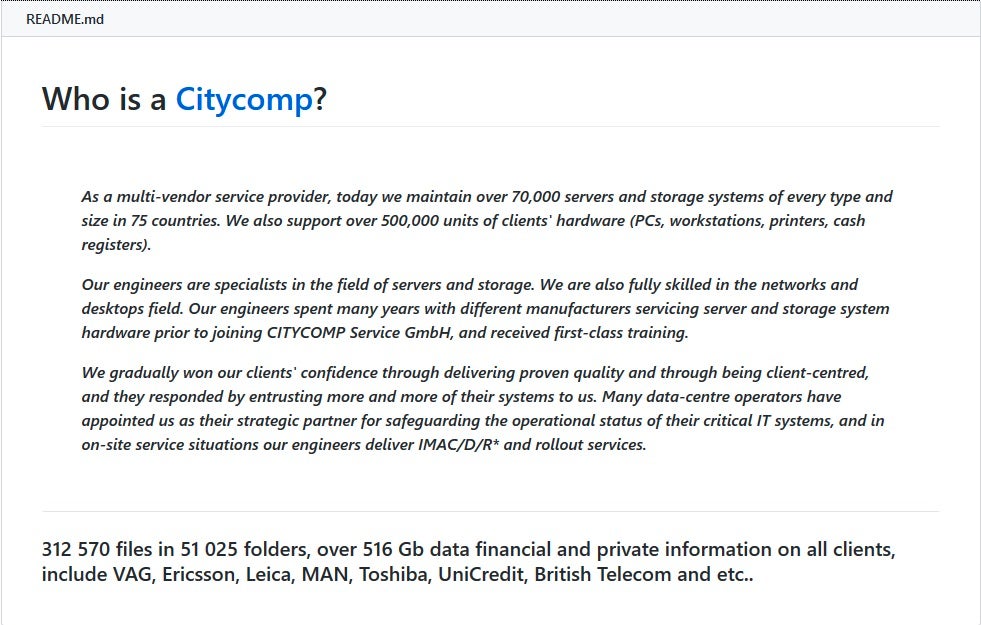
It should also be noted that Maze is not the only ransomware family that embraces this multi-pronged approach. It was not long ago that we saw the Snatch ransomware gang post a 500+ GB data dump, all looted from their breach of CITYCOMP Service GmbH.
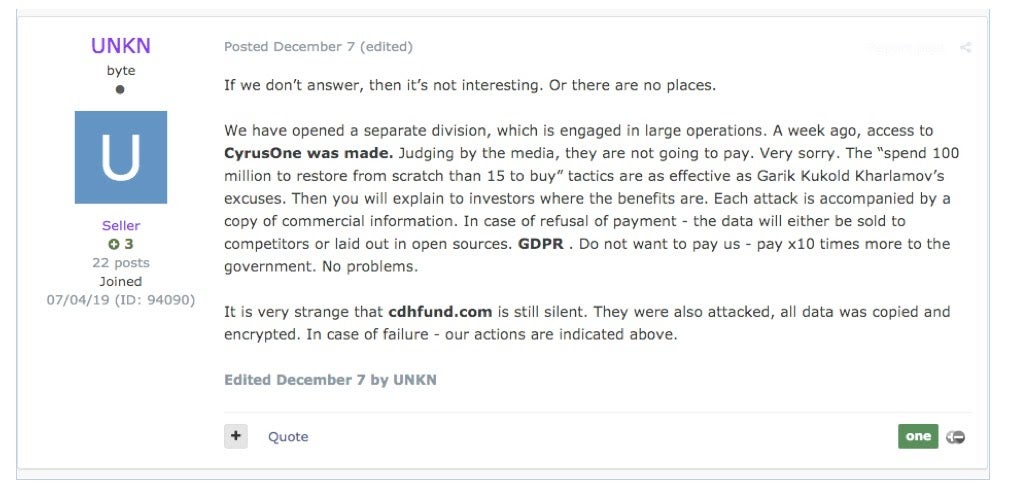
We have observed this with other highly-prolific families as well such as REvil (Sodinokibi). In the forum post shown below, we actually see an apparent “lead” in the REvil/Sodin group taking credit for the recent attack on CyrusOne and threatening to go forward with an approach similar to that of Maze.
Maze and Multi-Stage Malware Campaigns
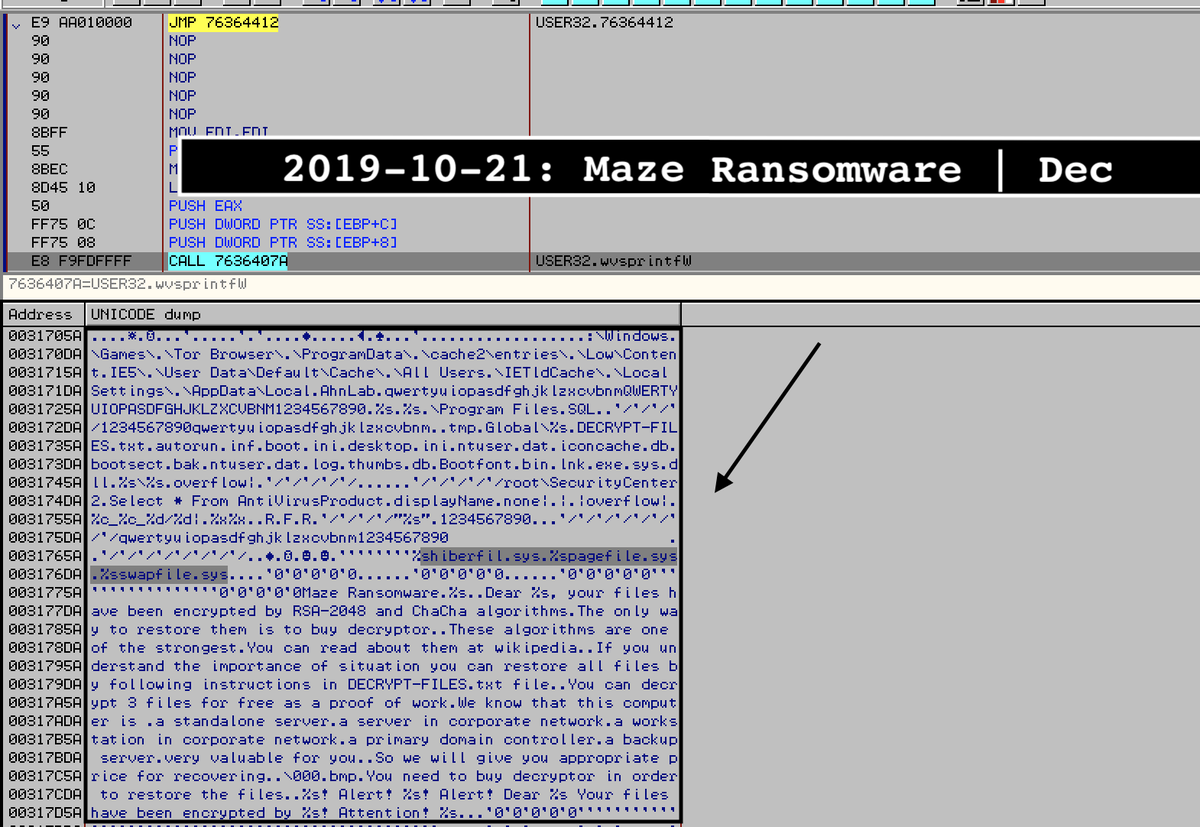
In addition, the delivery of the Maze ransomware is typically the 2nd or 3rd step in these campaigns. From the onset (mid-2019) to present day, the primary stage 1 delivery vector is phishing and spearphishing emails. Early campaigns were focused on using emails spoofed to appear to be from various Government entities. These include the United States Postal Service, German Federal Ministry of Finance, the Italian Ministry of Taxation, 1 & 1 Internet AG, and similar. These emails include a maliciously crafted document that has been weaponized to deliver a Cobalt Strike (Beacon) payload. With the Cobalt Strike payloads injected, the cybercriminals can then further traverse the target environment (move laterally) or pull-down additional tools and malware. In this case, the 2nd or 3rd stage malware is the Maze Ransomware. The ransomware versions contain whitelisted directories, boot and user files exclusions and anti-virus product grabber.
Starting with Cobalt Strike ensures enough persistence for the attacker to exfiltrate what they need, while maintaining a very low footprint on infected hosts. Cobalt Strike can also be used to directly handle the exfiltration tasks as well, although that is not always the case. If LOTL (Live off the Land) tactics can be employed, they will be.
Maze Goes Public With Victims’ Details
Moving to present day (mid-December 2019), the “Maze Crew” has gone fully public with a list of “non-compliant” victims. Currently, 11 companies are listed, along with various amounts of supporting data and “proof” of compromise. Typically, this is in the form of documents or raw databases specific to each environment. For each listed company, the amount of exfiltrated data is detailed, along with a table of specific hosts that the attackers not only encrypted but also extracted data from. Internal IP addresses, hostnames, and country/geo data are included as well.
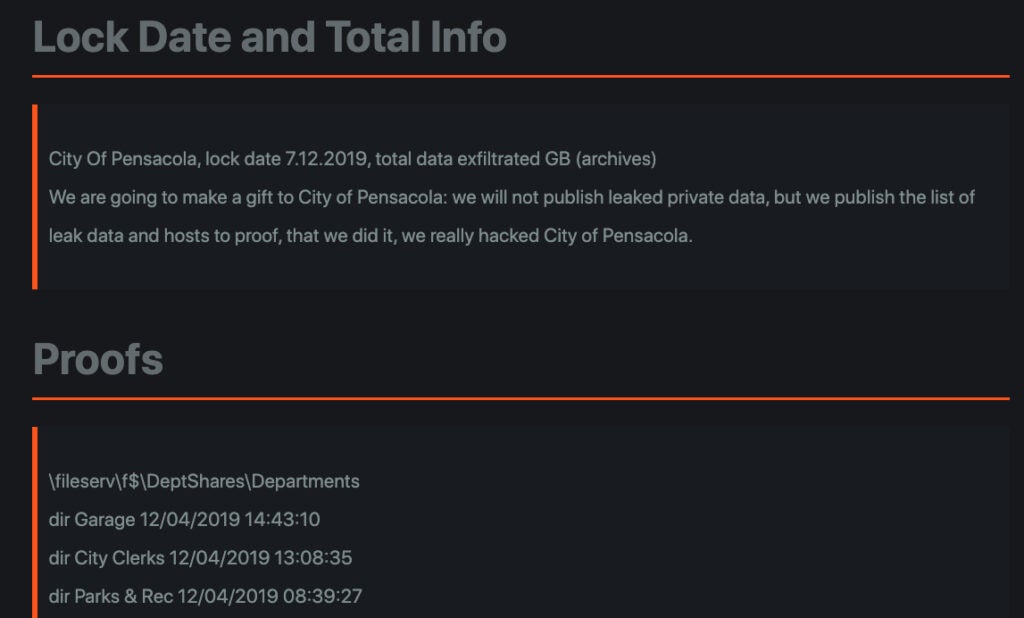
Not all data is provided for all victims, but from what is available we can see, at the very least, that several hundred GB of data could be released when time runs out for each of these companies. The victims come from a wide variety of industries including Distribution/Logistics, Food and Agriculture, Commercial Services & Products, Manufacturing, Insurance Services as well as Government entities.
Conclusion
Maze ransomware doesn’t just demand payment for a decryptor but exfiltrates victim data and threatens to leak it publicly if the target doesn’t pay up. This “double whammy” piles on yet more pressure to convince the victim to cave into the cybercriminals’ demand. As we’ve seen time and again, threat actors will use any and every trick they can to ensure a payday. The onus now is on businesses to make sure they have a trusted security solution proven to prevent ransomware from executing in the first place, as even the ability to restore data from a backup won’t save the day against this latest tactic in the criminals’ playbook.
Indicators of Compromise (IOCs):
SHA-256: 9d86beb9d4b07dec9db6a692362ac3fce2275065194a3bda739fe1d1f4d9afc7
SHA-256: 5c9b7224ffd2029b6ce7b82ea40d63b9d4e4f502169bc91de88b4ea577f52353
SHA-256: 4218214f32f946a02b7a7bebe3059af3dd87bcd130c0469aeb21b58299e2ef9a
SHA-256: fb5de69b222d81fea2f4b08fd5af612faf24b9e75698ac331af066fbc360a30a




